TLS for Media, Player, and API URLs
Introduction
Transport Layer Security (TLS) protects data transferred over the internet by encrypting it. (TLS replaced an earlier cryptographic protocol called SSL.) The process is largely transparent to users. Data delivered over the web can be delivered with or without encryption, so it is up to the client (a browser, for example) to signal to servers that data should be encrypted. This is usually done by using the HTTPS protocol for URLs instead of HTTP.
supports TLS for all media delivery on these terms:
- Those using Brightcove CDNs can Contact Brightcove Support to have their accounts configured for either HTTPS + HTTP delivery of data, or for HTTPS-only delivery.
- Those using other CDNs (sometimes called BYO CDNs) can request these options from their CDN (if they are supported, which is likely).
Whether you need TLS depends mainly on whether the site(s) and pages(s) where you deploy your videos load over HTTPS - if they do, then your videos and video assets, as well as players and API requests must also be requested over HTTPS; if they do not, they may fail to load or generate warnings in the viewer's browser.
Changes in TLS support
Following the recommendations of internet security experts, Brightcove change its support for versions of TLS as detailed below.
What is the change?
is gradually ending support for TLS versions 1.0 or 1.1. Customers using these versions must migrate as soon as possible.
Support for TLS 1.0 and 1.1 has been turned off for the:
- Gallery APIs
- Delivery System API
- Player Management API
- Ingest APIs (
https://ingest.api.brightcove.comandhttps://ingestion.api.brightcove.com)
Why is Brightcove deprecating older TLS versions?
The security of customer data is a top priority for Brightcove. These changes are unfolding across our industry, and many of our technology partners and peers have already taken the steps to disable early TLS.
How do I know if our systems are ready for this change?
As TLS 1.0/1.1 are deprecated, connections with the platform will need to use the TLS 1.2 encryption protocol (or later). We expect the impact to be minimal, but there are two areas of risk:
- You should make sure that all connections to the APIs (e.g., a call from a Python script to the CMS API) are made from platforms that support TLS 1.2 or later. This means that automated processes should be hosted from a compatible platform.
- Your users may be impacted if they are using an unsupported browser, if they have disabled the relevant encryption protocols, or if they are using an unsupported device.
In general, the impact should be limited to older devices and browsers that represent a small fraction of our users. Please see below for a sample of unsupported clients and devices.
Unsupported Platforms (Players/SDKs)
As noted before, HTTP connections (unencrypted) are unaffected by the change. Below find a list of user agents where HTTPS connections using TLS 1.2 are not supported.
OS/Browser Combinations
- Windows 7[1-1] / Chrome 29 (or earlier Chrome versions)[1-2]
- Windows 7[1-1] / Firefox 10.10.12, Firefox 17.0.7, Firefox 24.2.0, Firefox 22, Firefox 24[1-2]
- Windows 8 / Firefox 26
- Windows XP[1-1] / IE 6[1-3]
- Windows Vista[1-1] / IE 7[1-3]
- Windows Phone 8.0 / IE 10[1-3]
- Windows 7[1-1] / Opera 12.15, Opera 15, Opera 16[1-4]
- OS X 10.6.8 / Safari 5.1.9[1-2]
- OS X 10.8.4 / Safari 6.0.4[1-2]
- Android 4.3 or earlier
Notes
- [1-1] Windows versions earlier than Windows 8 are not supported by Brightcove
- [1-2] Brightcove supports only the current version, and two earlier major releases of browsers
- [1-3] Brightcove does not support any version of IE (Internet Explorer)
- [1-4] Brightcove does not support any version of Opera
Other Unsupported Platforms and Devices
You should verify integrations on platforms and devices where we do not provide a player or SDK, or where they have authored a custom integration with our APIs. The list below is not meant to be exhaustive, but includes a number of platforms and OEM devices that do not support TLS 1.2.
Software Libraries and Runtime Environments
- Java 6u45
- Java 7u25
- OpenSSL 0.9.8y
Smart TV/OEM Devices
- 2015 Panasonic CS650 TV
- 2014 Sharp TV - UD20, U20, US20, W20, W25, R30, XL20, G20
- Playstation 3
- Playstation Vita
Enabling TLS 1.2
In some cases, TLS 1.2 may be supported but disabled. To enable TLS 1.2 protocols on Windows web browsers, please see below.
Microsoft Internet Explorer
- Open Internet Explorer.
- From the menu bar, click Tools > Internet Options > Advanced tab:
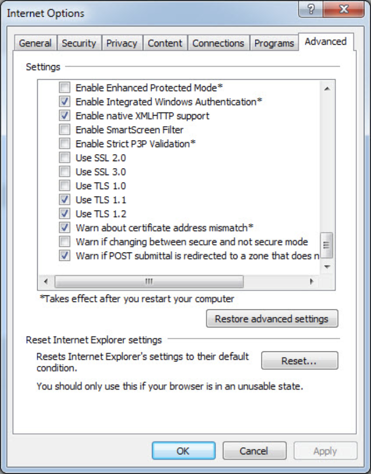
Internet Explorer Settings. - Scroll down to Security category, manually check the option box for Use TLS 1.2.
- Click OK.
- Close your browser and restart Internet Explorer.
Google Chrome
- Open Google Chrome.
- Click Alt-F and select Settings.
- Scroll down and select Show advanced settings.
- Scroll down to the Network section and click on Change proxy settings.
- Select the Advanced tab.
- Scroll down to Security category, manually check the option box for Use TLS 1.1 and Use TLS 1.2.
- Click OK.
- Close your browser and restart Google Chrome.
Mozilla Firefox
- Open Firefox.
- In the address bar, type about:config and press Enter.
- In the Search field, enter
tls. Find and double-click the entry forsecurity.tls.version.max. - Set the integer value to 3 to force protocol of TLS 1.2.
- Click OK.
- Close your browser and restart Mozilla Firefox.
Opera
- Open Opera.
- Click Ctrl plus F12.
- Scroll down to the Network section and click on Change proxy settings.
- Select the Advanced tab.
- Scroll down to Security category, manually check the option box for Use TLS 1.1 and Use TLS 1.2.
- Click OK.
- Close your browser and restart Opera.
